Recently a member
posted in the forums about a new ransomware that was appending the
.surprise extension to encrypted files. When I received the sample, I learned that what I had was an loader that executed a heavily modified
EDA2 ransomware variant from memory. That was interesting enough, but soon reports started coming in that the those who were infected were being done so via TeamViewer connections.
The first ransomware installed via TeamViewer?
As more reports started to come in from Surprise victims, a disturbing trend was discovered. All of the victim's had TeamViewer installed and
logs showed that someone connected to their machine using TeamViewer and uploaded the
Surprise.exe files to their desktop.
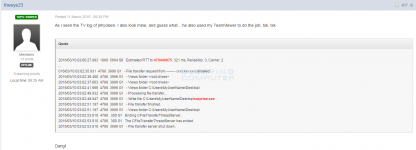
Post showing a TeamViewer Log
As more logs were posted, it could be seen that there were two TeamViewer IDs that were used by the attackers to upload the ransomware to the computer and execute it. These IDs were
479441239 and
479440875.
Once it was discovered that TeamViewer was involved, I immediately reached out to TeamViewer support to try and get someone who was part of their security team to either call me or email me so we could discuss this attack.Talking to one of the security team members, I was told that the associated IDs have already been disabled so that they could no longer be used on TeamViewer. I was also told, that it appears that the connections made by the ransomware developer were using the credentials of the victim. TeamViewer felt that some of these accounts may have been included in account dumps, where their credentials were retrieved by the ransomware devs.
On checking various databases, I did find that more than half of the victims were listed on the
https://haveibeenpwned.com/ site.
At this point, the Surprise ransomware appeared to have gone dark, so we are unable to investigate this further.