DROWN Attack — More than 11 Million OpenSSL HTTPS Websites at Risk
Kompletter Artikel: The Hacker News - DROWN Attack — More than 11 Million OpenSSL HTTPS Websites at Risk
http://www.bleepingcomputer.com/new...ly-encrypts-your-data-but-also-speaks-to-you/

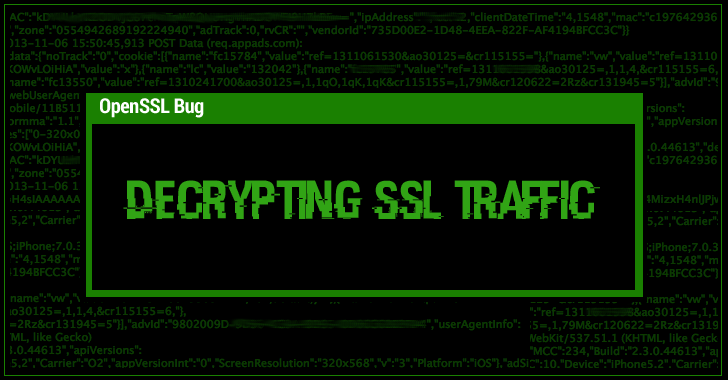
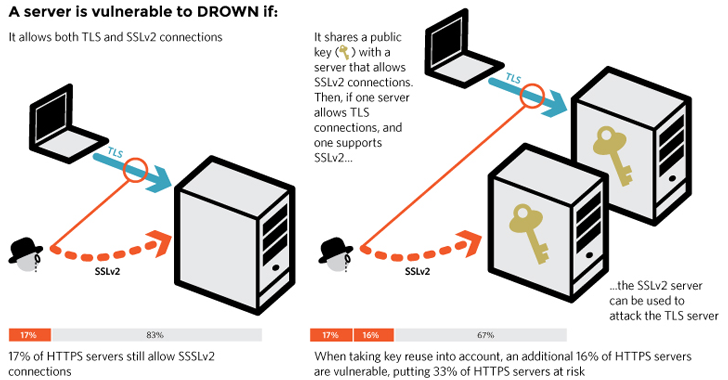
A new deadly security vulnerability has been discovered in OpenSSL that affects more than 11 Million modern websites and e-mail services protected by an ancient, long deprecated transport layer security protocol, Secure Sockets Layer (SSLv2).
Dubbed DROWN, the highly critical security hole in OpenSSL was disclosed today as a low-cost attack that could decrypt your sensitive, secure HTTPS communications, including passwords and credit card details…
...and that too in a matter of hours or in some cases almost immediately, a team of 15 security researchers from various universities and the infosec community warned Tuesday.
Kompletter Artikel: The Hacker News - DROWN Attack — More than 11 Million OpenSSL HTTPS Websites at Risk
Zuletzt bearbeitet: